Mark Giles (talk | contribs) |
Mark Giles (talk | contribs) No edit summary |
||
| Line 372: | Line 372: | ||
yourrxmart.ru |
yourrxmart.ru |
||
yoursafemall.ru |
yoursafemall.ru |
||
| − | * Another common string is "lucky" |
||
| − | luckyhealingdeal.ru |
||
| − | luckyherbdeal.ru |
||
| − | luckyherbmarket.ru |
||
| − | luckyherbmart.ru |
||
| − | luckyherboutlet.ru |
||
| − | luckyherbreward.ru |
||
| − | luckyherbssupply.in |
||
| − | luckyhotshop.ru |
||
| − | luckymedssale.trade |
||
| − | luckymedssupply.ru |
||
| − | luckynaturalinc.ru |
||
| − | luckypharmdeal.ru |
||
Other common naming strings are "hot", "magic", "medical", "medicinal", "natural", "online", "organic", "perfect", "pure", "remedial", "safe", "secure", "smart", "trusted" |
Other common naming strings are "hot", "magic", "medical", "medicinal", "natural", "online", "organic", "perfect", "pure", "remedial", "safe", "secure", "smart", "trusted" |
||
Revision as of 10:11, 12 July 2019
Description
 Bulker.biz homepage, Sept. 2008 |
 Evapharmacy.ru homepage, July 2010 |
EvaPharmacy (previously known as Bulker.biz) is the organization which sponsors spammers to promote sites within what has previously been referred to as the Yambo Financials group of web properties. These include My Canadian Pharmacy, International Legal RX, Canadian Health&Care Mall, US Drugs, Canadian Family Pharmacy, Canadian Family Pharmacy, Toronto_Drug_Store, RxExpressOnline, RxMedications and others.
This was learned from postings on bulkerforum.biz by username "ebulker", who would invite users to promote for their properties.
Please note that as of late 2008, they changed their domain name to bulkerbiz.com, since a rash of domain shutdowns terminated the bulker.biz domain. bulkerbiz.com still showed all the original branding of bulker.biz.
Bulkerbiz.com is now also terminated. On or around April 14th, 2009, bulkerbiz.com suddenly announced that they were yet again changing domains, leaving the ICQ address of the individual known as "ebulker" [333192431].
Site is closed. Please contact ICQ 333192431 for new address.
According to Knujon and LegitScript, the brands previously part of the Bulker.biz affiliate program are now part of an operation called "EvaPharmacy."
Eva Pharmacy brand websites were first discovered in 2007 loading content from Bulker.biz sites. User EvaPharmacy made the first announcement of an affiliate program by that name on the antichat.ru forum in November 2009.
Although the public terms of service for EvaPharmacy state that spamming is not permitted, the affiliate program buys ad banners on forums like antichat.ru, on which members openly discuss spamming and hacking.
The website for Bulker.biz, in contrast, openly advertised that affiliates were permitted to spam.
Acquisition of new spammers / mailers
Here is a posting from Mar. 14th, 2007 found on bulkerforum.biz, posted by ebulker. It directly connects this operation to the abovementioned sites, and outlines their commission structure:
ebulker Joined: 19 Sep 2006 Posts: 28 Posted: Wed Mar 14, 2007 10:00 am Post subject: Bulker.biz newsletter for February 2007. Last news: - New portal "Men's Health" is going to be launched next Monday! - "My Canadian Pharmacy" redesign will be rounded off soon. - Next popular products were added in February: norvasc, zyban, cymbalta ====== Features of Bulker.biz ========= Resemble our feautures: 1. Daily payouts for all the affiliates (or on demand) 2. We pay wires, WebMoney, and Fethard 3. Popular sites with a great choice of products and high ratio (beginning from 1:30) 4. 5% referral system 5. Free personal domains (ability to add your domains to our servers) 6. We pay probable refunds & chargebacks ourselves 7. Live support (icq, skype messenger & e-mail) 8. "Bonus Timer" program. Bonus-money for the three best affiliates EVERY DAY 9. Free geocities accounts ================ TOP Products ============================= - Viagra - Cialis Soft - Cialis + Viagra - Viagra Soft - Cialis - Ambien - Soma - HGH ================ TOP Domains =============================== - yahoo.com - aol.com - hotmail.com - comcast.net - sbcglobal.net - cox.net - earthlink.net - bellsouth.net - msn.com - gmail.com Best Regards, Bulker.Biz Team Mailto: support@bulker.biz ICQ: 333192431 Skype: BulkerSupport _________________ Bulker biz is: - 40% affiliates comission - Lot of very popular pharma products - Daily payments All you need for huge earnings! ICQ: 333192431; e-mail: support@bulker.biz
Hijacked Unix / Linux Servers
As discussed in the My Canadian Pharmacy entry in detail, Bulker.biz domains used in their spam campaigns were all hosted via hijacked, publicly owned Unix or Linux servers without their owners' knowledge or consent. This is achieved by gaining root access to these poorly-secured and often abandoned servers, and installing two custom-written Unix binaries known (as of this writing) as "tirqd" and "uirqd". These binaries act as proxy web hosts, drawing content from an as-yet-unknown third party server (tirqd), and a DNS proxy server (uirqd), often providing DNS services for hundreds of spamvertisable domains. This renders the cost of their web hosting to virtually zero, since they are in fact stealing the bandwidth from an unwitting third party who is unaware that their server has been compromised in any way.
Identity Theft and Credit Card Fraud
Bulker.biz / EvaPharmacy domains are routinely registered using the identity of an unwitting third party, using their name, address and phone number, and registering using their credit card. Information gathered via independent research has shown that in many cases these individuals are very ill and not computer literate, and often don't know what "domain registration" is. This research is ongoing but has uncovered several hundred such individuals who were unaware their contact information was used for the WHOIS data for hundreds of illicit "My Canadian Pharmacy" (and other bulker.biz / EvaPharmacy property) domains.
Notably the email address is always one which someone or some group at bulker.biz / EvaPharmacy have created to handle email questions only.
Unlawful practices
Drug Enforcement Administration
From DEA Consumer Alert
READ THIS BEFORE PURCHASING PRESCRIPTION DRUGS OVER THE INTERNET !!!
DEA Warning--Buying drugs online may be illegal and dangerous!
Federal law prohibits buying controlled substances such as narcotic pain relievers (e.g., OxyContin®, Vicodin®), sedatives (e.g., Valium®, Xanax®, Ambien®), stimulants (e.g., phentermine, phendimetrazine, Adderall®, Ritalin®) and anabolic steroids (e.g., Winstrol®, Equipoise®) without a valid prescription from your doctor. This means there must be a real doctor-patient relationship, which by most state laws requires a physical examination. Prescriptions written by "cyber doctors" relying on online questionnaires are not legitimate under the law.
Buying controlled substances online without a valid prescription may be punishable by imprisonment under Federal law. Often drugs ordered from rogue websites come from foreign countries. It is a felony to import drugs into the United States and ship to a non-DEA registrant.
Buying drugs online may not be only illegal, but dangerous. The American Medical Association and state boards of medicine and pharmacy have all condemned the practice of cyber doctors issuing online prescriptions as unacceptable medical care. Drugs delivered by rogue websites may be the wrong drugs, adulterated or expired, the wrong dosage strength, or have no dosage directions or warnings.
DEA is targeting rogue online pharmacies for prosecution and shutting down these illegal websites.
Food and Drug Administration
The FDA is working with a global law enforcement consortium -
- World Customs
- Department of Justice
- Interpol
- National health and law enforcement agencies from 99 participating countries
They have been vigorously pursuing the Eva Pharmacy sites, and using their powers to seize some of the more prevalent domains.
Examples of seizures:
- www.canadianfamilypharmacy.net
- www.canadianhealthandcaremall.com
- www.canadianneighborpharmacy.com
- www.canadian-neighbor-pharmacy.net
- www.canadian-neighbor-pharmacy.net
They have issued a June 2013 press release explaining the operation.
Products Bulker.biz / EvaPharmacy promotes
The list of products known to be promoted by this sponsor are:
- Canadian Health&Care Mall
- My Canadian Pharmacy
- RxMedications
- RxExpressOnline
- Canadian Neighbor Pharmacy
- Toronto Drug Store
- Canadian Family Pharmacy
- International Legal RX
- US Drugs
- US Pharmacy
- VIP Pharmacy ("Viagra + Cialis")
- Men Health (Men+ Health, Men's Health)
- WikiPharmacy
- Nutrition Mall (November 2016)
- Indian Pharmacy
- OEM Software
- Exclusive Caviar Online
- Double Your Dating
When the Eva Pharmacy domains are set up as web sites, there are common factors which show that they are from the same people, the Eva Pharmacy gang.
As at November 19, 2014, most of these operations transferred to the same web server to perform the check-out operation.
They all transferred to the same site, safecheckoutrx.com with variations on the prefix
- checkoutwbaxvbsy.safecheckoutrx.com/cart/checkout/
- checkoutxzwtucrc.safecheckoutrx.com/cart/checkout/
- checkoututdeyfzt.checkoutservicerx.com/cart/checkout/
- checkoutwdebtuas.safecheckoutrx.com/cart/checkout/
Domain Name: SAFECHECKOUTRX.COM Registrar: CJSC REGISTRAR R01 Registrant Name: Privacy protection service - whoisproxy.ru.
On November 23 2014 the checkout site was changed to smartpaymentrx.com on the same Russian registrar and the same Russian privacy protection.
It can be seen that Russian registrar R01.RU who protects over 1,650 Eva pharmacy fraud domains, and also protects the checkout operation.
Brands going through this checkout include
- Men's Health
- WikiPharmacy
- US Drugs
- Toronto Drugstore
- Canadian Family Pharmacy
- Canadian Neighbor Pharmacy
- My Canadian Pharmacy
- Canadian Health&Care Mall
The site has an SSL certificate issued by COMODO RSA and the connection uses 128-bit TLS 1.2 encryption issued Nov 19 2014 to *.safecheckoutrx.com with expiry Nov 20 2015.
An examination of the IP addresses of the name servers across the fraud families show that they are residing on the same IPs. Take one example, IP 111.93.156.204
ns1.androidtablethealthcare.com ns1.bioportfoliohealthcaretab.com ns1.boschwelness.com ns1.bplispills.com ns1.careipad.com ns1.dronelispills.com ns1.drugslevitrapills.com ns1.fivere.ru ns1.fowy.ru ns1.fvecare.com ns1.gademn.ru ns1.garagesalerx.com ns1.healthcaresearchandmarkets.com ns1.healthflu.com ns1.marijuanamedicaltab.com ns1.marijuanamedicalviagra.com ns1.medicalprescriptionpatients.com ns1.medicaltabgroup.com ns1.mediterraneanpharmacydiet.com ns1.myviagralevitra.com ns1.nagh.ru ns1.oshu.ru ns1.tabdietfat.com ns1.vasomaxgenerics.com ns1.xqgnkikh.com
All of these name servers are authoritative for the domains across all of the Eva Pharmacy categories. That means they are owned by the same people.
An examination of the IP addresses used for hosting these fraud domains shows that all families share the same IPs. Take for example address 188.112.149.11 - six of the families shared it in June 2016 -
- Canadian Family Pharmacy
- Canadian Health&Care Mall
- Canadian Neighbor Pharmacy
- My Canadian Pharmacy
- RxMedications
- RxExpressOnline
Common IP addresses
A quick way to verify these sites is to examine the hosting addresses. Note that * items have been removed. Many compromised hosts used for this operation during September 2020 - May 2021 were located at these IPs.
| - - - - - - - - - - - | - - - - - - - - - - - | - - - - - - - - - - - | - - - - - - - - - - - | - - - - - - - - - - |
|---|---|---|---|---|
| Live | ||||
| ---- | ||||
| 2.184.67.164 | 5.101.140.77 | 5.188.211.29 | 37.46.135.24 | 51.222.136.197* |
| 51.89.151.227 | 84.15.139.143 | 84.200.77.180 | 95.165.145.236 | 95.165.149.124 |
| 95.165.27.205 | 95.31.40.41 | 103.117.141.163 | 103.121.91.117 | 103.126.6.161 |
| 103.127.31.154* | 103.135.128.72* | 103.139.42.59 | 103.146.23.100 | 103.147.153.123* |
| 103.147.153.126* | 103.157.224.90 | 103.228.114.93 | 103.236.150.106* | 103.236.201.228 |
| 103.92.25.124 | 103.242.117.197 | 103.28.149.174 | 103.30.246.103 | 103.83.192.109 |
| 103.9.158.67 | 103.92.25.124 | 185.182.105.220 | 185.182.105.221 | 185.227.136.203 |
| 185.24.232.98 | 185.227.136.205 | 198.211.33.45 | 200.55.243.166* | 202.145.2.67 |
| Removed | ||||
| ---------- | ||||
| 5.133.12.16* | 5.181.158.179* | 5.181.158.181* | 5.187.52.1* | 5.187.52.12* |
| 5.187.52.13* | 5.187.52.9* | 5.2.89.72* | 5.253.62.111* | 5.45.82.242* |
| 31.132.1.40* | 37.61.211.187* | 37.61.211.188* | 37.61.211.189* | 45.119.41.11* |
| 45.119.41.12* | 45.119.41.14* | 45.125.65.93* | 45.131.83.10* | 45.137.21.144* |
| 45.137.21.166* | 45.67.116.219* | 45.86.163.7* | 51.158.23.140* | 51.210.134.178* |
| 51.38.80.31* | 58.64.137.69* | 62.141.56.196* | 78.157.200.139* | 80.233.134.248* |
| 80.233.134.249* | 81.4.110.230* | 82.199.101.248* | 82.199.101.44* | 82.199.104.3* |
| 85.17.219.96* | 85.183.104.125* | 85.254.72.7 * | 87.120.253.209* | 89.105.221.82* |
| 89.222.128.42* | 91.199.41.51* | 91.199.41.53* | 91.199.41.55* | 93.119.105.5* |
| 94.126.173.105* | 94.152.214.31* | 94.156.175.107* | 101.53.147.97* | 101.99.90.111* |
| 103.108.117.18* | 103.117.141.184* | 103.130.218.113* | 103.138.96.86* | 103.142.25.210* |
| 103.160.144.64* | 103.160.62.153* | 103.221.220.169* | 103.42.58.61* | 103.56.148.90* |
| 103.6.207.162* | 103.8.26.45* | 103.86.51.178* | 103.92.30.110* | 109.232.240.24* |
| 111.90.158.205* | 112.78.10.214* | 119.59.123.55* | 119.59.123.55* | 128.1.60.6* |
| 130.185.72.89* | 134.119.186.27* | 134.119.186.29* | 141.98.10.125* | 141.98.10.136* |
| 141.98.10.142* | 141.98.10.225* | 146.247.49.105* | 146.88.26.167* | 159.148.186.165* |
| 159.148.187.4* | 159.148.187.6* | 167.114.188.36* | 170.130.173.37* | 171.244.143.163* |
| 173.213.80.216* | 176.123.9.67* | 178.239.177.183* | 178.255.40.234* | 179.43.149.28* |
| 180.131.147.100* | 185.105.109.213* | 185.108.128.181* | 185.128.42.106* | 185.128.42.107 * |
| 185.128.43.18* | 185.128.43.21* | 185.128.43.54* | 185.130.206.6* | 185.140.249.133* |
| 185.183.104.123* | 185.216.8.156* | 185.227.136.206* | 185.24.232.118* | 185.24.232.134* |
| 185.24.232.76* | 185.9.158.36* | 185.99.3.68* | 185.99.3.80* | 194.5.179.140* |
| 195.123.247.36* | 198.27.110.97* | 209.127.28.5* | 209.97.184.221* | 212.34.158.134* |
| 212.34.158.134* | 213.226.100.10* |
Where to contact the compromised hosting ISP:
Abuse contact for '5.2.88.0 - 5.2.89.255' is 'alvaro.montero@ipcore.com' Abuse contact for '5.45.80.0 - 5.45.83.255' is 'abuse@ispiria.net' Abuse contact for '5.101.140.64 - 5.101.140.95' is 'abuse@ukservers.com' Abuse contact for '5.181.158.0 - 5.181.158.255' is 'abuse@mivocloud.com' Abuse contact for '5.133.8.0 - 5.133.15.255' is 'abuse@artnet.pl' Abuse contact for '5.187.48.0 - 5.187.55.255' is 'abuse@artnet.pl' Abuse contact for '5.188.211.0 - 5.188.211.255' is 'abuse@pindc.ru' Abuse contact for '5.253.60.0 - 5.253.63.255' is 'abuseto@adminvps.ru' (Removed) Abuse contact for '27.124.80.0 - 27.124.95.255' is 'abuse@medialink.net.id' Abuse contact for '31.200.247.0 - 31.200.247.255' is 'ripe@unelink.com' Abuse contact for '37.46.132.0 - 37.46.135.255' is 'abuse@abusehost.ru' Abuse contact for '45.67.116.0 - 45.67.116.255' is 'abuse@itns.md' Abuse contact for '45.86.163.0 - 45.86.163.255' is 'support@crowncloud.net' Abuse contact for '45.125.65.0 - 45.125.65.255' is 'abuse@tele-asia.net' Abuse contact for '45.131.83.0 - 45.131.83.255' is 'abuse@sered.net' Abuse contact for '51.89.148.0 - 51.89.151.255' is 'abuse@ovh.net' Abuse contact for '79.172.193.0 - 79.172.193.255' is 'abuse@deninet.hu' (Removed) Abuse contact for '80.233.134.0 - 80.233.134.255' is 'abuse@telia.lv' Abuse contact for '82.199.104.0 - 82.199.107.254' is 'abuse@seven-sky.net' Abuse contact for '84.15.136.0 - 84.15.143.255' is 'abuse@bi.lt' Abuse contact for '84.200.77.0 - 84.200.77.255' is 'abuse@accelerated.de' (Removed) Abuse contact for '85.254.72.0 - 85.254.72.255' is 'support@serveria.com' Abuse contact for '87.120.253.0 - 87.120.253.255' is 'abuse@neterra.net' Abuse contact for '89.105.192.0 - 89.105.223.255' is 'abusedesk@novoserve.com' Abuse contact for '89.222.128.0 - 89.222.131.255' is 'abuse@netorn.net' 'abuse@netorn.ru' Abuse contact for '80.233.134.0 - 80.233.134.255' is 'abuse@telia.lv' Abuse contact for '93.119.104.0 - 93.119.105.255' is 'abuse@virtono.com' Abuse contact for '94.152.0.0 - 94.152.255.255' is 'abuse@kei.pl' Abuse contact for '94.156.175.0 - 94.156.175.255' is 'abuse@iws.co' Abuse contact for '95.24.0.0 - 95.31.255.255' is 'abuse-b2b@beeline.ru' Abuse contact for '95.84.128.0 - 95.84.159.255' is 'abuse@rt.ru' Abuse contact for '95.165.128.0 - 95.165.255.255' is 'abuse@spd-mgts.ru' Abuse contact for '103.6.204.0 - 103.6.207.255' is 'yogie@redwhite.co.id' Abuse contact for '103.9.156.0 - 103.9.159.255' is 'cuong.trinh@vnso.vn' Abuse contact for '103.28.148.0 - 103.28.149.255' is 'support@easyway.co.id' Abuse contact for '103.56.148.0 - 103.56.149.255' is 'abuse@jagoanhosting.com' Abuse contact for '103.86.48.0 - 103.86.48.255' is 'abuse@bangmodhosting.com' Abuse contact for '103.92.24.0 - 103.92.27.255' is 'hm-changed@vnnic.vn' 'system@tlsoft.vn' Abuse contact for '103.117.141.0 - 103.117.141.255' is 'abuse@casbay.com' Abuse contact for '103.121.88.0 - 103.121.91.255' is 'tampd@bkns.vn' Abuse contact for '103.126.6.0 - 103.126.7.255' is 'shazim@serverstack.in' Abuse contact for '103.138.96.0 - 103.138.96.255' is 'hello@hostitsmart.in' Abuse contact for '103.146.22.0 - 103.146.23.255' is 'duc@lanit.com.vn' Abuse contact for '103.147.152.0 - 103.147.153.255' is 'abuse@shineservers.com' Abuse contact for '103.221.220.0 - 103.221.223.255' is 'hoanglong@azdigi.com' Abuse contact for '103.236.201.0 - 103.236.201.255' is 'admin@idcloudhost.com' Abuse contact for '111.90.128.0 - 111.90.159.255' is 'abuse@shinjiru.com.my' Abuse contact for '112.78.0.0 - 112.78.15.255' is 'vanht@ods.vn' Abuse contact for '130.185.72.0 - 130.185.72.255' is 'report@parspack.com' Abuse contact for '119.59.96.0 - 119.59.127.255' is 'abuse@metrabyte.cloud' Abuse contact for '141.98.10.0 - 141.98.10.255' is 'admin@serveroffer.lt' Abuse contact for '146.247.49.0 - 146.247.49.255' is 'abuse@netcetera.co.uk' Abuse contact for '159.148.186.0 - 159.148.186.255' is 'support@serveria.com' Abuse contact for '159.148.0.0 - 159.148.255.255' is 'abuse@latnet.eu' Abuse contact for '171.224.0.0 - 171.255.255.255' is 'hm-changed@vnnic.vn' 'soc@viettel.com.vn' Abuse contact for '176.123.0.0 - 176.123.11.255' is 'abuse@alexhost.com' Abuse contact for '178.239.176.0 - 178.239.177.255' is 'abuse@irideos.it' Abuse contact for '178.255.40.232 - 178.255.40.235' is 'abuse@artnet.pl' Abuse contact for '179.43.149.0/26' is 'support@privatelayer.com' Abuse contact for '180.131.144.0 - 180.131.147.255' is 'abuse@nawala.org' Abuse contact for '185.24.232.0 - 185.24.232.255' is 'abuse@servebyte.com' Abuse contact for '185.128.40.0 - 185.128.43.255' is 'abuse@rackend.net' Abuse contact for '185.130.206.0 - 185.130.207.255' is 'abuse@as61317.net' Abuse contact for '185.140.248.0 - 185.140.249.255' is 'contact@buzinessware.com' Abuse contact for '185.183.104.0 - 185.183.104.255' is 'abuse@m247.ro' Abuse contact for '194.5.176.0 - 194.5.179.255' is 'berbid238@gmail.com' Abuse contact for '200.55.243.166' is 'radhios@gmail.com' syt.com web page Abuse contact for '202.145.0.0 - 202.145.3.255' is 'abuse@uninet.net.id' Abuse contact for '209.127.0.0 - 209.127.138.255' is 'abuse@servermania.com'
Example of the highest used IP addresses from November 2020
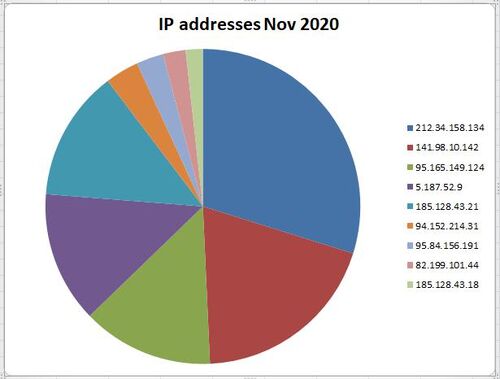
Sample sites
Here is a selection from over 500 live sites in Feb 2018, on the same IP
Domain name Fraud type Sponsoring Registrar bestbesteshop.com Canadian Health&Care Mall TUCOWS DOMAINS INC. bestcareinc.ru My Canadian Pharmacy R01-RU bestcuringstore.ru My Canadian Pharmacy R01-RU bestremedialsale.su Canadian Health&Care Mall R01-SU bestremedytrade.ru Canadian Neighbor Pharmacy R01-RU bestsafedeal.ru My Canadian Pharmacy R01-RU bestsmartassist.su Canadian Health&Care Mall R01-SU familydrugssale.ru Canadian Family Pharmacy R01-RU familyhotmall.ru Toronto Drugstore R01-RU fastbestsale.com US Drugs TUCOWS DOMAINS INC. fastbestvalue.ru CanadianPharmacy R01-RU fastcaremall.ru My Canadian Pharmacy R01-RU fastdrugsdeal.ru Canadian Family Pharmacy R01-RU fastfastprogram.com Canadian Neighbor Pharmacy TUCOWS DOMAINS INC. fastfastshop.ru Toronto Drugstore R01-RU fasthealthdeal.com My Canadian Pharmacy BIZCN.COM, INC. fastsafegroup.com CanadianPharmacy BIZCN.COM, INC. firstfirstdeal.ru Canadian Neighbor Pharmacy R01-RU firstherbwebmart.su CanadianPharmacy R01-SU firsthotassist.su CanadianPharmacy R01-SU firsthotmart.com Canadian Health&Care Mall BIZCN.COM, INC. firstpillsmart.ru Canadian Family Pharmacy R01-RU firstremedytrade.su Canadian Health&Care Mall R01-SU firstsafeeshop.ru My Canadian Pharmacy R01-RU graziakevina.ru Canadian Health&Care Mall R01-RU homeherbelement.com Canadian Health&Care Mall BIZCN.COM, INC. homeherbsreward.ru My Canadian Pharmacy R01-RU homeherbssale.ru Canadian Health&Care Mall R01-RU homehotmall.ru My Canadian Pharmacy R01-RU homemedsgroup.ru Canadian Health&Care Mall R01-RU
All of these frauds are registered with a subset of registrars, and at one time they all shared the same hosting IP address. This supports the statement that all frauds come from the same perpetrators.
Selection of registrars
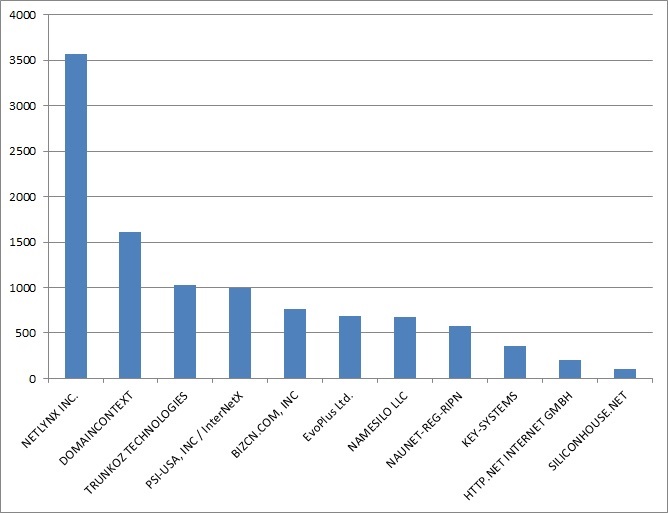
Each family of fraud is spread over a common subset of registrars. For example, over the 2015 year, the most frequently abused registrars for the highest spammed families have been
1764 PSI-USA, INC. DBA DOMAIN ROBOT (abandoned) 1749 TRUNKOZ TECHNOLOGIES PVT LTD. 1267 NETLYNX, INC. 978 NAMESILO, LLC (abandoned) 779 DOMAINCONTEXT, INC. 459 CLOUD GROUP LIMITED (abandoned)
1545 PSI-USA, INC. DBA DOMAIN ROBOT (abandoned) 1411 TRUNKOZ TECHNOLOGIES PVT LTD. 1026 NETLYNX, INC. (abandoned) 892 NAMESILO, LLC (abandoned) 370 CLOUD GROUP LIMITED (abandoned) 277 NAUNET-REG-RIPN
152 NAUNET-REG-RIPN 148 PSI-USA, INC. DBA DOMAIN ROBOT (abandoned) 114 TRUNKOZ TECHNOLOGIES PVT LTD. 91 NETLYNX, INC. (abandoned) 82 REGRU-REG-RIPN 68 CLOUD GROUP LIMITED (abandoned)
57 TRUNKOZ TECHNOLOGIES PVT LTD. 56 PSI-USA, INC. DBA DOMAIN ROBOT (abandoned) 23 NETLYNX, INC. (abandoned) 21 NAMESILO, LLC (abandoned) 10 CLOUD GROUP LIMITED (abandoned) 8 REGRU-REG-RIPN
26 PSI-USA, INC. DBA DOMAIN ROBOT (abandoned) 23 NETLYNX, INC. (abandoned) 11 NAMESILO, LLC (abandoned) 10 TRUNKOZ TECHNOLOGIES PVT LTD. 8 NAUNET-REG-RIPN 4 REGRU-REG-RIPN
By 2017/2018 some of these abused registrars were so effective in shutting them out, they were abandoned by the Eva perpetrators.
Naming patterns
Naming patterns are common across the whole family.
- One pattern comprises the concatenation of two forenames. For example -
abagaildaniele.ru abbyehildagarde.su abbyjenica.ru adalineirita.ru adanverina.ru adelheidcassandre.ru adelinakalindi.ru adoreeshandie.ru aggilibbey.ru anastasieviviana.ru andieannelise.ru andiedollelsa.ru andreiabagail.ru anettatamma.ru annabelahindasuzi.ru
- Another pattern concatenates medical terms.
For example -
drugslevitrapills.com healthflu.com bioportfoliotabhealthcare.com medtabletandroid.com opioidherbalmeds.com apptabletmed.com ipadlistablet.com
- This pattern uses a common string, eg "lucky"
luckybestmart.ru luckybestservice.ru luckycareelement.ru luckycuringmart.ru luckydrugdeal.win luckydrugmarket.ru luckydrugsale.ru luckyfastmart.ru luckyfirstgroup.ru luckygenericmart.ru luckyhealingdeal.ru luckyherbdeal.ru
- Another common string is "your"
youraidmart.ru yourbestinc.ru yourbestmall.com yourcaremall.ru yourpillvalue.trade yourprivateeshop.ru yourremedygroup.ru yourremedyvalue.ru yourrxmart.ru yoursafemall.ru
Other common naming strings are "hot", "magic", "medical", "medicinal", "natural", "online", "organic", "perfect", "pure", "remedial", "safe", "secure", "smart", "trusted"
The identification of common naming patterns further demonstrates that all of these brands of frauds belong to the same perpetrators - the Eva Pharmacy gang. These commonly named domains spread across the full Eva brand family -
Online Pharmacy Toronto Drugstore RxExpressOnline RxMedications Men's Health Canadian Family Pharmacy Canadian Neighbor Pharmacy CanadianPharmacy My Canadian Pharmacy Canadian Health&Care Mall
Summary of common factors
- 1. The same registrars are being selected with the same frequency by these perpetrators.
- 2. They are hosting their domains on the same common IP addresses.
- 3. All Eva Pharmacy name servers are authoritative for domains across the whole family.
- 4. The name servers across the whole family reside on the same IP addresses.
- 5. Domains follow a common naming pattern across the whole family.
Sample EvaPharmacy domains, brands and abused registrars
From December 2012 to August 2014 there has been a concerted anti-fraud campaign against these unlawful pharmacy domains. An historical list showing the domain names, brands and registrars providing the domain name service is listed above.
The data that the following table summarizes is on public display at the FraudReports web site with a "Rogues and Champions" summary table by registrar
A list of the most abused registrars, counting the frequency of occurrences of domain registrars, ordered by most to least frequent. The responsiveness is based on how many reports were acted upon, and how quickly.
| Registrar | Reputation |
|---|---|
| DOMAINCONTEXT | 100% compliant |
| CLOUD GROUP LIMITED aka UK2GROUP | 100% compliant |
| NICS TELEKOMUNIKASYON TICARET LTD.STI. | 100% compliant |
| REGRU-REG-RIPN / REG.RU | 100% compliant after one week delay |
| REGISTRYGATE GMBH | 100% compliant |
| UNITED-DOMAINS AG | 100% compliant |
| NIC.AT | 100% compliant |
| InterNetworX Ltd. & Co. KG | 100% compliant |
| LCN.COM LTD. | 100% compliant |
| NAMEBAY | 100% compliant |
| 0101 INTERNET INC. | 100% compliant |
| MAILCLUB SAS | 100% compliant |
| EURODNS S.A | 100% compliant |
| INTERNET.BS | 100% compliant |
| NEW DREAM NETWORK LLC | 100% compliant |
| TUCOWS DOMAINS INC. | formerly 100% compliant slow to act in 2018 |
| UA.SHOST / NIC.UA | 100% compliant |
| REGISTER.COM INC. | 100% compliant |
| KEY-SYSTEMS GMBH | 100% compliant slow to act in 2018 |
| TRUNKOZ aka OWNREGISTRAR | 100% compliant fastest response, under 6 hours |
| PSI-USA INC. DBA DOMAIN ROBOT aka INTERNETX | 100% compliant |
| NAMESILO LLC | 100% compliant |
| NETLYNX INC. | 100% compliant |
| HTTP.NET INTERNET GMBH | 100% compliant |
| PUBLIC DOMAIN REGISTRY PDR | 100% compliant slow to act in 2018 |
| TODAYNIC,COM, INC | 100% compliant |
| R01.RU | refuses to act 0% |
| BIZCN.COM, INC | responds to LegitScript and ICANN requests - very slow to act in 2018, 2-3 months |
| NAUNET-REG-RIPN | unresponsive and unhelpful (12 month expiries) 40% |
Registrar compliance
This graph shows the most number of fraud domains suspended by registrars