Background[]
His "name" is actually a series of aliases
- Alex Polyakov (the big Soviet spy character in John LeCarre's spy novel "Tinker, Tailor, Soldier, Spy")
- AlekseyB
- Kevin Benson
- Alex Blood
- Paul Gregoire
- David Learner
- Jack McDonald
- Gordon Metcalfe
- Alexander Mosh
- Aleksey Polyakov
- Gary Reed
- Gregory William
Spamhaus lists him as the number one cyber-criminal. He may or may not be a member of the well-known illegal spam operation Yambo Financials. But there is evidence that links the two. "Alex Polyakov" is the term used throughout this wiki to represent a crime syndicate comprising many individuals working in concert with each other.
McAfee Site Advisors posted against his sites are listing a chain of offenses:
Alex Polyakov spamvertises many sites, eg Canadian Health&Care, xynaVolume, VIP Pharmacy, Exquisite fake watches, Hoodia Life, HGH Life, My Canadian Pharmacy, International RX, US Drugs. He steals credit card information from web sites like this. Do not place an order. Find more information on this criminal by copying this link into your browser http://www.spamhaus.org/rokso/listing.lasso?-op=cn&spammer=Alex%20Polyakov He is currently ranked as the world's largest spammer typically accounting for approximately 12% of reported spam. At times he has accounted for upwards of 70% of reported spam. He is known for the following criminality: 1) Spamming 2) Investment scams 3) Fake bank and eBay phishing 4) Money laundering 5) Child porn (distribution, hosting, sales) 6) Running a botnet 7) Identity theft / credit card theft 8) Employment scams 9) Fake diploma scams 10) MySpace.com spamming 11) Bribing a French webmaster to host his sites 12) Domain kiting 13) Nameserver hijacking 14) Website hijacking
Sponsoring registrars[]
Reputable registrars will shut down Alex Polyakov's operations when presented with the overwhelming evidence of his crimes. There are now only a few registrars who are prepared to sponsor his fraudulent and illegal activities despite clear evidence of his gang's criminal operations. Three typical Polyakov name server groupings showing the crime sponsoring registrars are shown here:
| ns1.svedot.ru | NAUNET-REG-RIPN |
| ns2.polacrepox.com | XIN Net |
| ns2.tergiversationceq.com | Beijing Innovative |
| ns1.compaginationnej.com | Beijing Innovative |
| . | . |
| ns1.fetuas.ru | NAUNET-REG-RIPN |
| ns2.mopperwoc.com | XIN Net |
| ns1.edacitypur.com | Beijing Innovative |
| ns2.dicerreq.com | Beijing Innovative |
| . | . |
| ns1.vertow.ru | NAUNET-REG-RIPN |
| ns2.pianofortezih.com | XIN Net |
| ns1.consuetuderir.com | Beijing Innovative |
| ns2.guydefenseless.com | Beijing Innovative |
Registrars who remove his sites[]
Polyakov has been shut out by most reputable registrars all over the world. Registrars who have cooperated in removing his domain names on request include:
- Tucows
- Enom
- GANDI
- DSTR Acquisition
- Ace of Domains (until December 2006)
- Moniker (until December 2006)
- InterCosmos
- Misk
- CSL Computer Service (joker.com)
- Network Solutions
Registrars who knowingly sponsor his access[]
Registrars who have received numerous reports of Alex Polyakov's criminal activities but have failed to take effective action include:
- Ace of Domains (since December 2006)
- Moniker (since December 2006)
- Beijing Innovative
- Xin Net
Related spam operations[]
Sites known to be operated and spammed by this criminal organization are listed at Category:Yambo family.
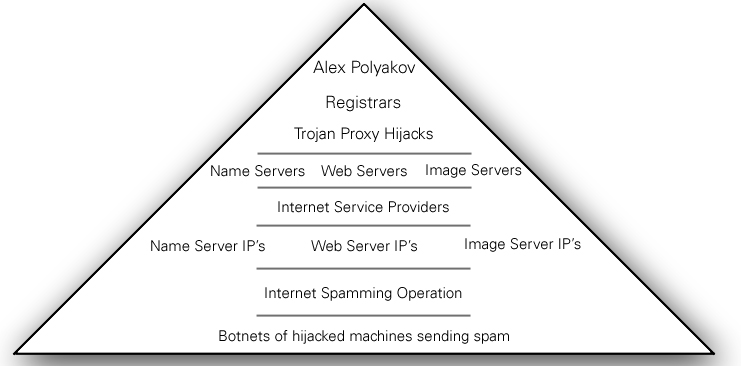
Method of operation[]
The following description applies to
Polyakov rarely pays for any service. He has developed trojan programs which he uses to provide
- a proxy name server
- a proxy web server
- a proxy image server
Rather than set up his own machines to run web sites, he steals from others. He scans for weak security on existing machines that are connected to the Internet. When he manages to locate machines with poor security, eg easily guessed passwords for the administrator, he puts them on his list. Subsequently, he will transfer one of his trojan programs onto his hijacked machine.
A user's web browser requests access to a Polyakov web site. The domain name of the web site has been registered with a domain name registrar. First of all the web site name must be translated into an IP address. Normally, this translation is performed by a domain name server, named something like ns1.example.com. In Polyakov's case, the request goes to a hijacked machine, which acts as a proxy and passes the translation request to a back-end domain name server. The domain name of the name server has been registered with a domain name registrar. The registrars for web servers and name servers have accepted a contract with a known criminal, and are his sponsors.
When a user accesses one of his pharmacy sites, the hijacked proxy web server passes requests for the web pages to a back-end web server. As the back-end web server forwards the web page back to the compromised machine, and then to the user, it has embedded calls to load the images for the page. The images are requested from a compromised image server. The image server in turn acts as a proxy, requesting the actual images from a back-end image server.
Thus, the three operations of domain name resolution, web server and image server are performed on hijacked machines without the consent or knowledge of their owners. He steals their computing resources, and their bandwidth.
Countermeasures[]
Polyakov knows that his methods are public knowledge, so he takes additional measures to counter attempts to close this operation down.
- He runs an automated registration program that creates hundreds of new DNS domains per day
- He rotates his compromised web server and image server machines at least once every 24 hours, sometimes every 8 hours
- He rotates his compromised name servers on a regular basis, somewhere between once a day and once a month
- He blocks any known enforcement agencies from access to his sites
- Drug Enforcement Agency (DEA)
- Federal Bureau of Investigation (FBI)
- Food and Drug Administration (FDA)
- Department of Justice (DOJ)
- He blocks companies who would have an interest in prosecuting him for breach of copyright
- Visa
- Mastercard
- Pfizer
- He blocks services that are used to track his operations
- DNSstuff.com
- Ironport (Spamcop)
- He blocks any site that retaliates persistently against his operation
- He registers his sites under up to 4 different name servers, spread over up to 4 different registrars making it necessary for all the registrars to act decisively to remove access to his sites
Known Name Servers[]
Alex Polyakov routinely creates domains which he uses as his domain name servers, usually running them as a trojan proxy on an illegally hijacked machine. To avoid being complicit in his crimes, registrars should have no hesitation in removing these immediately or on request.
Examples of his known name servers are
| ns1.adonoput.com | ns1.amylaceouswer.com | ns1.asderdub.com | ns1.barasincle.com | ns1.belikeyous.com |
| ns1.bestdrugshere.info | ns1.bsophunt.com | ns1.charteredbol.com | ns1.cluvditch.com | ns1.excentriccod.com |
| ns1.fastundslow.com | ns1.fatbast.com | ns1.ferrywend.com | ns1.fondnessyup.com | ns1.gietunsp.com |
| ns1.goddtraulism.com | ns1.grettnos.com | ns1.grisaillesag.com | ns1.groupron.com | ns1.guardlessrod.com |
| ns1.peckdore.com | ns1.perceivablenut.com | ns1.poertodas.com | ns1.renedrop.com | ns1.rupponce.com |
| ns1.selidoff.net | ns1.sendsafedns.com | ns1.seveopd.com | ns1.terkclass.com | ns1.theblackrains.net |
| ns1.tonsilsbot.com | ns1.tyroidont.com | ns1.uiltonthe.net | ns1.upgoandstay.com | ns1.vigilupanka.com |
| ns1.xetopnet.com | ns1.zafferbod.com | ns2.adonoput.com | ns2.amylaceouswer.com | ns2.asderdub.com |
| ns2.barasincle.com | ns2.belikeyous.com | ns2.bestdrugshere.info | ns2.bsophunt.com | ns2.charteredbol.com |
| ns2.cluvditch.com | ns2.excentriccod.com | ns2.fastundslow.com | ns2.fatbast.com | ns2.ferrywend.com |
| ns2.fondnessyup.com | ns2.gietunsp.com | ns2.goddtraulism.com | ns2.goodiman.com | ns2.grettnos.com |
| ns2.grisaillesag.com | ns2.groupron.com | ns2.guardlessrod.com | ns2.hortonhop.com | ns2.jokutnap.com |
| ns2.jotokio.info | ns2.lebee4ae.com | ns2.leoforever.com | ns2.loerjamm.com | ns2.matronizeer.com |
| ns2.misterboby.com | ns2.mucronated.com | ns2.neokalvinw.com | ns2.obtundert.com | ns2.ourboycot.com |
| ns2.padguide.info | ns2.peckdore.com | ns2.perceivablenut.com | ns2.poertodas.com | ns2.renedrop.com |
| ns2.rupponce.com | ns2.selidoff.net | ns2.sendsafedns.com | ns2.seveopd.com | ns2.stwiev.com |
| ns2.terkclass.com | ns2.tetscope.com | ns2.theblackrains.net | ns2.tonsilsbot.com | ns2.tyroidont.com |
| ns2.uiltonthe.net | ns2.upgoandstay.com | ns2.vigilupanka.com | ns2.xetopnet.com | ns2.zafferbod.com |
| ns1.fatiloquent.com | ns1.practicekiss.net | ns1.norchikmik.com |
| ns1.driedoutdns.com | ns2.driedoutdns.com | ns1.hairyolddns.com | ns2.hairyolddns.com |
| ns1.surprisingdns.com | ns2.surprisingdns.com | ns1.ferygoins.com | ns2.ferygoins.com |
| ns1.chambogos.com | ns2.chambogos.com | ns1.dnsjig.com | ns2.dnsjig.com |
| ns1.twodogdns.com | ns2.twodogdns.com | ns1.abbcds.com | ns2.abbcdns.com |
| ns1.nastypq.com | ns2.nastypq.com | ns1.sonhtj.com | ns2.sonhtj.com |
Name Server hierarchy[]
By performing a whois with any Polyakov web site, you can determine its name servers. By recursively performing whois lookups on the domains of the name servers, you can climb up the hierarchy of Polyakov name servers, and find the relationships tying together his various illegal operations. Here are some examples of such hierarchies, starting from the top and working down. Bear in mind that these are all spammer owned domains, and that the top 3 in each case (sportystuuff.com, dnswhoisgood.com, dnsgoldone.com) are already known to be Alex Polyakov's domains, as are dnsfortherest.com and liquidhamdns.com
- sportystuuff.com
- dnswhoisgood.com
- dnsgoldone.com
- dnsfortherest.com
- liquidhamdns.com NS for many refinance spam sites (comufnterred.com onetkodthree.com blockdkfrme.com buttfosewme.com cavecfunone.com mayfornever.com toybflokss.com banfkfrost.com plumkr.com etc)
- dnsfortherest.com
- dnsgoldone.com
- dnswhoisgood.com
- sportystuuff.com
- dnswhoisgood.com
- dnsgoldone.com
- surprisingdns.com NS for many pharmacy and fake watch sites, HGHLife, HoodiaPlus, Exquisite Replica
- dnsgoldone.com
- dnswhoisgood.com
- sportystuuff.com
- dnswhoisgood.com
- dnsgoldone.com
- ferygoins.com NS for many pharmacy and fake watch sites, HGHLife, HoodiaPlus, ED Pill Store, Exquisite Replica
- dnsgoldone.com
- dnswhoisgood.com
- sportystuuff.com
- dnswhoisgood.com
- dnsgoldone.com
- chickdnsone.com NS for many refinance spam sites (alenkekwith.com piewonivetwo.com nnesaperz.com sgmykrtoutt.com ewtwooeztnoodle.com oratorncerely.com devokniappytodai.com etc)
- dnsgoldone.com
- dnswhoisgood.com
- sportystuuff.com
- dnswhoisgood.com
- dnsgoldone.com
- dnsjig.com NS for many pharmacy and fake watch sites, ED Pill Store, Exquisite Replica
- dnsgoldone.com
- dnswhoisgood.com
- sportystuuff.com
- dnswhoisgood.com
- dnsgoldone.com
- dnspotato.com NS for many pharmacy and fake watch sites, ED Pill Store, BugreLife, Exquisite Replica
- dnsgoldone.com
- dnswhoisgood.com
Thus, Alex Polyakov's related portfolio of illegal scam sites are revealed through his name servers.
Respective registrars have removed the upper end of this hierarchy, such as sportystuuff.com, dnswhoisgood.com, dnsgoldone.com, but the lower end awaits action from the remaining registrars who are still upholding their service contracts with this criminal, effectively sponsoring the crimes.
Registrant Examples[]
Any registrar should immediately revoke the access from any domain that is registered using these details.
Paul Gregoire gregoirep@coldmail.ca 175 Montreal Road suite 304 Vanier, Ontario K1L 6E4 Canada +001.6132552162
Paul Gregoire (paulgreg@smxbox.com) 1-613-482-5333 Fax: 175 Montreal Road #304 Ottawa, Ontario K1L 6E4 CA
Paul Gregoire (paulgreg@walla.com) +1.6132552162 Fax: 175 Montreal Road #304 Vanier, ONTARIO K1L 6E4 CA
Note: The above address is a strip club called "The Playmate Club."
jack mcdonald 380 Crete Place vanier, ON (CA) K1L7K8 613-255-2162 jackmcdo@coldmail.ca
Note: the real telephone number for Jack McDonald at this address is (613)-742-7652
Gregory William 1808 Bowen road 109 Nanaimo, BC V9S 5W4 CA gregw@coldmail.ca (604)767-8695
Note: the above address is a dental clinic for which the real telephone number is (250)-754-9903 .
Gregory William (paul-greg@coldmail.ca) +1.6047678695 Fax: 3200 North Island Highway Nanaimo, BC V9T 1W1 CA
gregory william 1808 Bowen road suite 109 V9S5W4 nanaimo Ontario Canada +1.6047678695 gregw@coldmail.ca
Note that Nanaimo is in British Columbia, not Ontario
gary reed garyr@coldmail.ca 3495 Cambie Street 150 vancouver BC V5Z 4R3 CA Phone: +1.6047678695
benson, kevin kevben@coldmail.ca 1098 Queen St halifax, nova scotia B3H 2R9 CA 902-412-1798
gordon metcalfe 7622 Elbow drive calgary, AB T2V 1K2 CA gordomet@coldmail.ca (140)364-04214
DLInt david learner (dlearn@coldmail.me.uk) +44.7005938354 Fax: +44.7005938354 11 Hillview Gardens Hendon London, ST NW4 GB
Contact Verification[]
In late 2006, attempts were made to contact Paul Gregoire using the data present in numerous WHOIS records.
Paul Gregoire
The street address (175 Montreal Road) is a strip club located in Vanier, Ontario, Canada (a suburb of Ottawa, Ontario) called "The Playmate Club." (Playmate Club listing)
It gets lots of popular reviews from patrons and is apparently not at all hard to find.
There is, obviously, no "#304". That building has only one storey.
The phone number changes every few months. As of this writing the phone number for Paul Gregoire is listed as (613) 255-2162. While the number is real, nobody at that number has ever heard of Paul Gregoire and they were dismayed to discover that their phone number was being abused in this way.
The most recent email address for Paul Gregoire (gregoirep@coldmail.ca) is a genuine address, but no response ever results from sending a message to it.
Gary Reed
The postal address for a recently spammed website was listed as 3495 Cambie Street, 150, Vancouver, BC, V5Z 4R3, CA.
3495 Cambie Street is in the middle of a residential neighborhood and turns out to be a UPS Store (formerly a Mail Boxes Etc. location.) Nobody at that UPS store would verify that anyone named Gary Reed had ever used a drop box at their location.
The phone number was most recently listed as (604) 767-8695. Upon calling it, you always get voicemail, and its outgoing message merely says the name "Gary.... Reed" in a very slow, precise voice. Other times that same phone number leads to a voicemail box which is constantly "full".
Emails to the email address garyr@coldmail.ca receive no reply, though it does appear to be a genuine address.
Coldmail.ca appears to be the free-email-provider of choice for this operation. In late June of 2007, that domain had gone down, after previously posting that it would be out of commission for a period of "maintenance." Several dozen new spammed domains continued to be created using coldmail.ca addresses for their contact email. At present, coldmail.ca no longer exists. All registrants using that as an e-mail address therefore contain deliberately misleading and outdated whois information. As ICANN stipulates that a registrar must be able to contact a registrant by e-mail, this in itself is grounds for suspension.